Java Programs For Udp Client And Server
- The client side implementation for java multi-cast communication is exactly same as general UDP, only the socket instance will be of MulticastSocket class. On the other hand, for server-side implementation, one extra step will be to join the multicast group as below.
- $ javac udp_server.java && java udp_server Server socket created. Waiting for incoming data. Now the udp server is up and waiting for incoming data. To check that udp server is really up, the netstat command can be used.
- Socket Programming in Java This article describes a very basic one-way Client and Server setup where a Client connects, sends messages to server and the server shows them using socket connection. There’s a lot of low-level stuff that needs to happen for these things to work but the Java API networking package (java.net) takes care of all of.
- A Simple Java UDP Server and UDP Client September 17, 2008 / 44 Comments / in Code Samples, Java, Software / by Dave For a class I am taking, we are testing out a simple UDP Server and UDP Client to demonstrate what each one does and how sockets work.
- Udp Client Server Example
- Java Programs For Udp Client And Server Server
- Windows Udp Client
- Java Udp Client Thread
- Java Programs For Udp Client And Server Windows 10
Introduction
Java UDP Client Server Program Not Working Apr 18, 2014. I am currently writing two java classes (client and server). The client takes an input number form keyboard and sends it to the server. The server then multiplies this number by two and sends it back to the client.
Separate processes (not threads) on the same computer may share dataand synchronize via pipes. For example,
pipes the output of ls to the input of grep using the UNIXpipe() function that sets up a one-way data flow from one process toanother.
But, what about connecting processes on separate computers? Javaprovides access to OS sockets (originally from BSD) that allow twoor more processes on the same or different computers to send/receivedata.
Background
IP
First, IP protocol. IP is an addressing and fragmentation protocol.It breaks all communications into packets, chunks of data up to65536 bytes long. Packets are individually routed from source todestination. IP is allowed to drop packets; i.e., it is an unreliableprotocol. There are no acknowledgements and no retransmissions.There is no flow-control such as there is in a RS-232 serialinterface.
One way to think of IP communication is by analogy to communicationsvia a letter. You write the letter (this is the data you are sending);put the letter inside an envelope (the IP packet); address theenvelope (using an IP address); put your return address on theenvelope (your local IP address); and then you send the letter. Likea real letter, you have no way of knowing whether an IP packet wasreceived. If you send a second letter one day after the first, thesecond one may be received before the first. Or, the second one maynever be received.
IP uses IP addresses to define source/target. IPs are 32 bitnumbers represented as 4 8 bit numbers separated by periods. When youtry to visit www.cnn.com in your browser, the computer must firsttranslate www.cnn.com to an IP address. Then the browser can make aconnection to the web server on the target machine identified by theIP address. You can think of this as the 'phone number' of a machine.Special IPs:
- Behind firewalls, people often use 192.168.x.y and use NAT(network address translation) in their firewall to translate anoutside address (a real IP) to the special IPs behind the wall. Agood security feature to hide your machines from outside. Forexample, all machines from within IBM's firewall probably look likethe exact same IP address to the outside world (for example, in web serverlog files). That is one reason you cannot use an IP address toidentify 'sessions' for a web server application.
- 127.0.0.1 is 'localhost'
Here is a simple Java program that prints out the current machines IPaddress and the address of jguru:
This is similar to doing:
UDP
UDP (User Datagram Protocol) is a connectionless protocol sittingon top of IP that provides unreliable packet delivery. Itessentially provides user-level access to the low-level IP hardware.But adds port numbers and checksumming for error handling (UDP candrop bad packets).
- UDP packets arrive out of order possibly or even not at all.
- The target/recipient does not acknowledge receipt
- there is no control (e.g., packets can arrive faster than therecipient can process them).
Useful for games (sending position), network time services, internettelephony, DNS, streaming video.
UDP is much faster than TCP.
TCP
TCP (Transmission Control Protocol) is another protocol, a reliablebut slower one, sitting on top of IP. TCP provides reliable,stream-oriented connections; can treat the connection like astream/file rather than packets. Packets are ordered into the propersequence at the target machine via use of sequence numbers. TCPautomatically deals with lost packets before delivering a complete'file' to a recipient. Control-flow prevents buffer overflows etc..
TCP is like a phone connection versus the simple 'fire and forget'letter stateless style of UDP. TCP sockets are open for the durationof a communication (i.e., until you close the connection).
Unlike UDP, the destination host and port number is not sufficient toidentify a recipient of a TCP connection. There are five distinctelements that make a TCP connection unique:
- IP address of the server
- IP address of the client
- Port number of the server
- Port number of the client (data goes out a socket from source too)
- Protocol (UDP, TCP/IP, etc..)
where each requested client socket is assigned a unique port numberwhereas the server port number is always the same. If any of thesenumbers is different, the socket is different. A server can thuslisten to one and only one port yet talk to multiple clients at thesame time!
What is a socket?
If the IP address is like an office building main phone number, asocket is like the extension numbers for offices. So the IP andsocket, often called the port, uniquely identify an 'office' (serverprocess). You will see unique identifiers like 192.168.2.100:80where 80 is the port. Just like in an office, it is possible noprocess is listening at a port. That is, there is no server waitingfor requests at that port.
Ports run from 1.65535. 1.1024 require root privileges to use andports 1.255 are reserved for common processes like:
- 80: HTTP
- 110: POP
- 25: SMTP
- 22: SSH
Continuing the office analogy further, just because you can open aconnection to a port doesn't mean you can speak the right language.Processes at ports all speak a specific, predefined, agreed-uponprotocol like HTTP.
You can use telnet to connect to ports to manually speak theprotocol. The most successful and long-lived protocols are simple andtext based.
Here I connect to the POP server at jguru:
Sockets and Security
Because sockets are the means by which computers on a networkcommunicate, they open your computer to attack. The simplest possibleattack is a denial of service just like a telemarketer that callsyou at home incessantly. Another common attack is to exploit avulnerability in a particular program listening at a port. Sometimesit's possible to trick a listening server program into allowingunauthorized access to that program or even the whole computer. Thehacker either wants data on the server or wants to use the machine asa mule (launch further attacks from that machine to (a) make itdifficult to trace back to the hacker and (b) launch multiplesimultaneous attacks).
The single most common vulnerability in server software is probablybuffer overflow. By overwriting a buffer, the software crashes, isconvinced to allow access, or execute some code sent by the hacker,thus, providing access. Here is a simple C program that illustrateshow a single buffer overflow can crash a server. The program willmost likely never return from function gone(), depending on theoperating system and compiler:
The array a has two chars but you are overwriting it by 1 char.That array is allocated on the stack instead of the heap (viamalloc()) and so you are overwriting the stack activation record forgone(). When gone() hits the return instruction, it will mostlikely not see a valid return address as gone() has stepped on it.Here is what happens when I compile and run it on a linux box:
You don't get consistent results and, once, the program never eventerminated!
 Differentiated: easier texts with questions in English, harder texts with more questions, advanced texts with questions in Spanish Professionally recorded with native speakers Click on the links below to listen to the texts, questions and answers for three of the 150 texts. Differentiated Revision Podcasts for GCSE Spanish 'The different formats give an incredible range of possibilities, for use in class, out of lessons, etc. The range of grammatical structures is wide and engaging, and there is the right level of challenge and differentiation.
Differentiated: easier texts with questions in English, harder texts with more questions, advanced texts with questions in Spanish Professionally recorded with native speakers Click on the links below to listen to the texts, questions and answers for three of the 150 texts. Differentiated Revision Podcasts for GCSE Spanish 'The different formats give an incredible range of possibilities, for use in class, out of lessons, etc. The range of grammatical structures is wide and engaging, and there is the right level of challenge and differentiation.
Languages with automatic runtime array bounds checking such as Javamake buffer overflow attacks impossible by their very nature, butlanguages like C are easy targets. This should highlight an importantfact about languages such as Java, C#, and Python. When there is anerror, you know it's an algorithmic problem. You could not havecorrupted the runtime system as you can in C/C++.
Firewalls
A firewall is a piece of hardware or software that blocks orrestricts access to a port on a computer or set of computers. Forexample, the SMTP port on our USF servers is not visible to machinesoutside the firewall. Our firewall(s) filter out incomingmachine:port requests that are dangerous. You can even set a firewallto stop connections to the SMTP server when a virus attachment issuspected. Another very common filter is for ssh connections. Forexample, at jGuru, we only allowed ssh connections to our live serversfrom certain IP addresses (machines in our office). The ssh port isopen, but only to certain machines. A random machine on the netcannot get to the ssh port.
One can also use a firewall to filter outgoing requests. For example,some companies stop all outgoing HTTP requests except from a singleproxy machine. Browsers must pass all HTTP traffic through thisproxy machine to get outside the wall. In this manner, a company cantrack and/or stop its employees from accessing certain websites.
How can peer-to-peer systems allow connections through firewalls? Inother words, if Sriram works behind a firewall blocking instantmessenger chat port x at BEA and Terence works at a firewall at USFblocking port x, how can Sriram and Terence chat client-to-clientinstead of doing their jobs? The only solution is for both of them tocontact a central server outside the wall(s) and have traffic routedthrough that central server. Even if Sriram's computer sends his IPaddress to the central server, there is no way Terence can open aconnection to that IP address from outside Sriram's firewall.Peer-to-peer systems such as this, that must operate in the presenceof firewalls, are really client-server architectures.
Java Sockets and Client/Server Programming
You can use Java to communicate with remote processes using aclient/server model. A server listens for connection requests fromclients across the network or even from the same machine. Clients knowhow to connect to the server via an IP address and port number. Uponconnection, the server reads the request sent by the client andresponds appropriately. In this way, applications can be broken downinto specific tasks that are accomplished in separate locations.
The data that is sent back and forth over a socket can be anything youlike in text or binary. Normally, the client sends a request forinformation or processing to the server, which performs a task orsends data back. You could, for example, place an SQL shell on theserver and let people talk to it via a simple client 'chat' program.
The IP and port number of the server are generally well-known andadvertised so the client knows where to find the service. In contrast,the port number on client the side (the outgoing socket) is generallyallocated automatically by the kernel.
Here is an example talking to the web server in CS department (port80). The protocol is 'GET /index.html' which directs the web serverto get contents of the index.html file at the document root and sendthe text back to you.
Creating a server
Java makes socket programming extremely easy. To create a serverlistening for requests, all you need to do is create a ServerSocketobject attached to a port number and call method accept(). Forexample, port 8080:
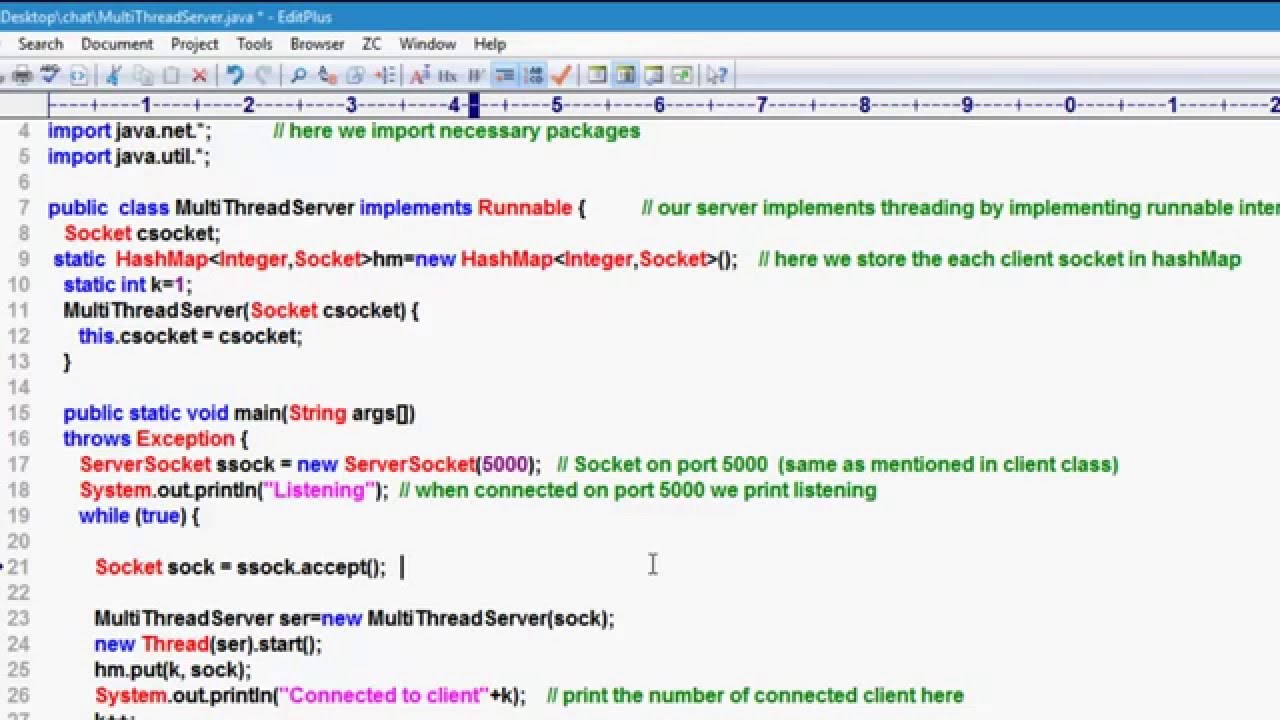
Method accept() returns when a client has connected to your server.The channel socket has a different port number than 8080. Theserver socket is 8080 so to get more than one person talking to theserver at once, the server needs to hand off socket connections to adifferent port.
You can get input/output streams from the channel socket to have aconversation with the client:
If you read from the input stream, you'll hear what the client has tosay. You can respond by sending data out the output stream.
Finally, don't forget to close your streams and socket:
Bola Soccer is a well-designed soccer game that you can play here on CrazyGames.com directly in your browser. This amazing sports game uses Flash to run in modern browsers. Bola Soccer has received 123,078 plays and has been rated 9.2 out of 10 with 2,116 votes. Mainkan game bola liga indonesia ini? Sekarang anda bisa memainkan liga super Indonesia online disini. Panggil teman mu dan rasakan bermain permainan asli indonesia! Legenda Sepak Bola 2016. Bermain 94109 kali. Tak seorang pun yang benar-benar tahu bagaimana bermain sepak bola seperti juara di Legenda Sepak Bola 2016! Bola Game, Pick a team, choose your colors and get ready to kick your way to glory. Game bola ps2 liga indonesia. Game bola terbaik - Game sepak bola menjadi salah satu jenis game terpopuler di dunia saat ini. Banyak game bola terbaru yang dirilis tiap tahunnya. Mulai dari Liga Inggris, Liga Spanyol, Liga Italia hingga Liga Champions. Cheat The Warriors PS2 Lengkap.
Creating a client
To talk to a server, open a socket to the machine and port:
Udp Client Server Example
When this returns, you can get input/output streams:
Java Programs For Udp Client And Server Server
The client's input stream is pulling from the server's output streamand vice versa.
An Example
Windows Udp Client
You can think of client/server programming like a pizza-deliveryplace. As an employee at the pizza place, you wait by the phone (youare the 'server'). Upon receiving a call from a client, you send a'hello' message. The client responds by sending you an order. Youacknowledge and write down the order (performing the server's task).You or they hang up (connection closes). Typically the server willspawn a thread to actually handle the request as it can becomplicated, like making the pizza. The server should go back toanswering the phone rather than using a single-threaded model andmaking the pizza itself. Note: the server blocks waiting on a requestat the port rather than sitting in a spin loop, 'picking up the phone'to see if anybody is there--it waits for a 'telephone ring.'
Java Udp Client Thread
The following code embodies a simple, single-threaded version of theabove scenario (it assumes ASCII text communication).
Java Programs For Udp Client And Server Windows 10
When we get to threads you will learn how to allow the pizza to bemade while the phone is being answered. It is like hiring more thanone employee.